Enterprise Security Features
Anava is built for enterprise deployments with comprehensive identity, access management, and compliance capabilities. This document outlines the security features available for enterprise customers.
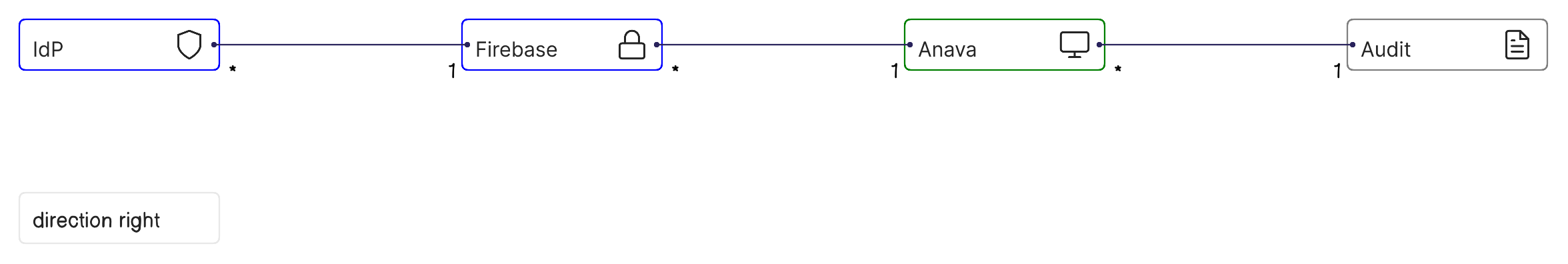
Identity & Access Management
Role-Based Access Control (RBAC)
Anava enforces strict authorization boundaries using a four-tier role hierarchy. Each role inherits permissions from lower tiers, ensuring consistent access control across the platform.
| Role | Scope | Typical Usage |
|---|---|---|
| Admin | Organization-wide | User management, security policy, device provisioning, full platform access |
| Operator | Operational | Device management, event handling, alert configuration, day-to-day operations |
| Viewer | Read-only | Monitoring, reporting, audit reviews, stakeholder visibility |
| Pending | Restricted | New accounts awaiting administrator approval |
Permission Categories:
- User Management: Invite users, approve pending accounts, modify roles
- Device Operations: Register devices, update configuration, retire cameras
- Event Access: View live feeds, review historical events, export data
- System Configuration: Modify organization settings, manage integrations
Multi-Factor Authentication (MFA)
Anava supports multi-factor authentication to protect against credential compromise.
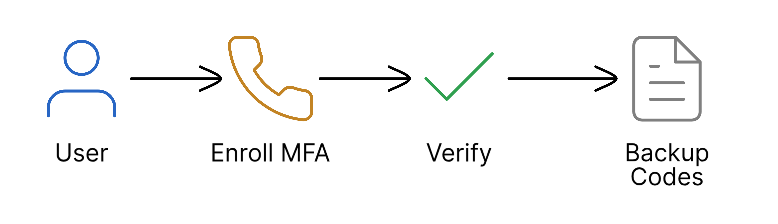
Supported Methods:
- TOTP (Time-based One-Time Password): Compatible with Google Authenticator, Authy, Microsoft Authenticator, and other RFC 6238-compliant apps
- SMS Verification: One-time codes delivered via SMS for backup authentication
Enforcement Options:
- Organization-wide MFA requirement (all users must enroll)
- Role-based enforcement (require MFA for admin and operator roles)
- Optional MFA (users can enable at their discretion)
Configurable Session Timeout
Anava provides user-configurable session timeout with compliance-safe defaults.
Available Options:
| Timeout | Use Case | Compliance |
|---|---|---|
| 5 minutes | Maximum security for sensitive operations | Exceeds all requirements |
| 10 minutes | High security, minimal interruption | PCI-DSS, SOC 2 compliant |
| 15 minutes | Balanced security and usability | PCI-DSS maximum for cardholder data |
| 30 minutes | Standard security for general use | SOC 2 compliant (maximum allowed) |
Role-Based Defaults:
- Admin users: 15 minutes (PCI-DSS compliant by default)
- Operator/Viewer users: 30 minutes
Compliance Coverage:
- PCI-DSS 8.1.8: Maximum 15 minutes for cardholder data access
- SOC 2 CC6.1: Automatic session termination after inactivity
- NIST 800-53 AC-11: Session lock after inactivity period
Users can customize their timeout in Settings > Security > Session Timeout. Changes take effect immediately across all active sessions.
Single Sign-On (SSO)
Enterprise customers can integrate Anava with their existing identity providers.
Supported Protocols:
- SAML 2.0: Integration with enterprise identity providers (Okta, Azure AD, OneLogin, Ping Identity)
- OpenID Connect (OIDC): Modern authentication with OAuth 2.0-based providers
Benefits:
- Centralized user provisioning and deprovisioning
- Consistent authentication policies across your organization
- Reduced password fatigue for end users
- Automated compliance with organizational security policies
SSO configuration is available for enterprise plans. Contact sales for setup assistance.
Multi-Tenancy
For organizations managing multiple sites or subsidiaries, Anava supports logical tenant separation.
Capabilities:
- Isolated data boundaries between tenants
- Tenant-specific user directories
- Cross-tenant administrative oversight (for parent organizations)
- Per-tenant customization and branding
Multi-tenancy is available for enterprise deployments. Contact sales for architecture consultation.
Audit & Compliance
Activity Logging
All security-relevant actions are logged immutably for audit and compliance purposes.
Events Tracked:
- User authentication (sign-in, sign-out, MFA events)
- Role and permission changes
- Device registration and deregistration
- Configuration modifications
- Data access and exports
Log Attributes:
| Field | Description |
|---|---|
| Timestamp | ISO 8601 formatted event time |
| Actor | User or service account performing the action |
| Action | Specific operation performed |
| Resource | Target of the action (user, device, setting) |
| Status | Success or failure with reason |
| IP Address | Source IP for user-initiated actions |
Retention & Export:
- Configurable retention periods (30-365 days based on compliance requirements)
- JSON export via API for SIEM integration
- Real-time webhook delivery for security monitoring tools
Compliance Certifications
Anava is designed to support enterprise compliance requirements.
Standards Supported:
- SOC 2 Type II: Security, availability, and confidentiality controls
- GDPR: Data protection and privacy controls for EU operations
- PCI-DSS: Relevant controls for retail and payment environments
Infrastructure:
- Built on Google Cloud Platform with inherited compliance certifications
- Identity Platform with 99.95% availability SLA
- Data residency options for regional compliance requirements
See Compliance for detailed compliance documentation.
Device Security
Hardware-Backed Identity
Anava leverages Axis camera hardware security for device authentication.
IEEE 802.1AR (Secure Device Identity):
- Factory-provisioned X.509 certificates in Axis Edge Vault TPM
- Private keys never leave the camera hardware
- Cryptographic proof of device authenticity
Benefits:
- Prevents device impersonation and spoofing
- Enables zero-touch provisioning
- Eliminates shared secrets and password management
See PKI Authentication for technical details.
Encrypted Communications
All data in transit is encrypted using industry-standard protocols.
| Channel | Protocol | Encryption |
|---|---|---|
| User to Platform | HTTPS | TLS 1.3 (AES-256-GCM) |
| Camera to Cloud | mTLS | TLS 1.2+ (mutual authentication) |
| Internal Services | Private API | TLS 1.3 |
Service Level Guarantees
Platform Availability
Anava provides enterprise-grade availability guarantees.
| Component | SLA Target |
|---|---|
| Web Application | 99.9% |
| API Services | 99.9% |
| Identity Services | 99.95% (Google Identity Platform) |
| MQTT Broker | 99.5% |
See SLA/SLO Targets for detailed service level documentation.
Support Tiers
| Tier | Response Time | Availability |
|---|---|---|
| Standard | 24 hours | Business hours |
| Premium | 4 hours | 24/7 |
| Enterprise | 1 hour | 24/7 with dedicated support |
Getting Started
To enable enterprise features for your organization:
- Contact Sales: sales@anava.ai for enterprise plan pricing
- Security Review: We provide security questionnaire responses and SOC 2 reports
- Architecture Consultation: Our team helps design your deployment topology
- Onboarding: Dedicated support for SSO integration and user migration
For implementation details and technical integration guides, enterprise customers can access Internal Documentation with an authorized account.